When I visit my website I am receiving a warning that my site contains malware. What is this and how can I remove this warning?
When a browser detects a website has having malware/phishing content it will usually alert the visitors with a big red splash page. The purpose of this to to make visitors aware that the website might contain malware or possibly content trying to steal sensitive information from the visitor.
In the event that your website is showing this warning it is likely that your website has been compromised.
Before we dive into how to clean up the website and request blacklist removal let’s show an example of a common warning page that could be shown on different web browsers:
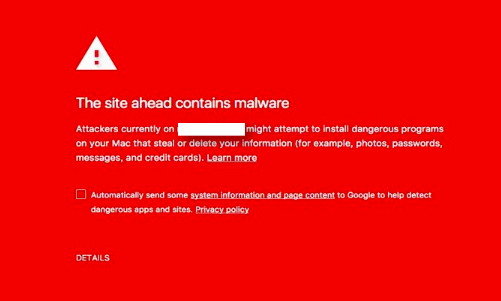
The above image is an example of a website detected as having malware in the browser Google Chrome. The warning page may contain different content between different browsers, but will usually be similar.
Step 1: Detect source of compromised site
Knowing that your website most likely is compromised due to the warning provided by Google, or possibly other web browsers, it is very important to detect the source of the compromise.
If you do not find how the compromise occurred in the first place, then there is no guarantee that you will not run into this issue again, as a security hole might exist on your website that attackers can exploit.
A majority of compromised websites are due to vulnerabilities in the website software that the site uses such as WordPress, Joomla, Drupal, Magento and other common CMS software. Popular CMS applications are targeted very heavily by attackers as they know they have a higher chance of breaking their way into the website if the software is not kept up to date.
There could be other ways the attacker got in, so we’ll include the below list for you to work off of:
-
Compromised Software - Check CMS applications to ensure they are up-to-date. The plugins/theme components are just as important to keep up to date. Custom written websites are still vulnerable, as they just aren’t as highly targeted.
-
FTP Credentials - Check your FTP logs to ensure the compromised did not occur through one of your accounts. If you have saved FTP credentials in an FTP client on your local computer, then you might make sure your computer isn’t infected with malware.
-
Control Panel Credentials - If access to your control panel has been stolen, then an attacker could have direct access to the file manager for the website.
-
Outdated Server Software - If using a scripting language that is versions behind, or no longer supported (EOL), then we recommend upgrading to a later version. For example, we’ve seen websites running ColdFusion 9 or 10 become compromised due to that version of CF no longer receiving security patches.
As a general rule of thumb you want to:
-
keep your website and server software up to the latest versions.
-
keep any and all credentials completely secure and use strong password requirements.
-
Use excellent AntiVirus software on any computers connecting to your websites files, regardless whether this is via the control panel, FTP accounts, or direct server access.
-
Step 2: Cleaning the Website From Malicious Files
Once you find the security hole, as mentioned above, make sure that you take the appropriate actions to close the vulnerability. Once done, then the next step would be cleaning up any malicious files on the website.
The majority of compromised websites have files hidden in several directories and it is important to note that every last file that has either been uploaded or modified by the attacker will need to be removed. If a single file remains on the website, it is possible the attacker could use this file to re-upload multiple other files to the website again.
In fact, a majority of websites that experience a compromise normally experience the same issue more than once due to not fully cleaning up the website as needed. When an attacker is placing files on your website, usually they will place a good number of backdoor scripts that allow them to regain access in case of an attempt of cleanup on the website.
Backdoor Shell File - A file that acts as a File Manager of sorts, allowing the attacker to view/change/upload files in the website.
Most attackers upload .PHP scripts to gain access to your websites file structure, as attackers know that the majority of web servers support the PHP scripting language.
A key tip for searching for these files is understanding that the attackers in question are smart. They will add some files to the website that are obvious as being placed by the hacker. They usually do this on purpose, so that you only scan your website for similar files. This makes the website owner ignore a file they believe is actually a part of their website. In some cases, the file might be a part of their website that was just modified by the attacker in some way.
If you are truly going to clean your website you will need to follow the steps below:
If using WordPress see our guide on cleaning up a compromised WordPress website.
-
Make a backup of the existing website, so you have this for safe keeping (should never use it as a restore point, though).
-
Remove ALL files from your website including any sub-folders.
-
Restore the website files from source.
Source - A fresh copy of the website files that has no modifications or additional files placed by an attacker. If using a CMS software, then this would be downloading a fresh version of that software and re-installing this on your website. If you took backups of your website prior to the hack, then this would work as well.
It is important to note that an attacker usually uploads key backdoor files weeks or sometimes months prior to the rest of the files that lead to the notice of compromise, so backups taken a week or two prior to noticing the compromise normally will not work, as that backup would contain malicious files as well.
-
If you are restoring from a backup taken previously, then we recommend first ensuring that this copy of your website is clean.
-
If you are using CMS software and are only doing a fresh re-install of the file structure (not the database), then we recommend ensuring that the database itself is clean as well. There are plugins for most common CMS applications that offer the functionality of scanning your database for Malware.
Alternative Option: One-Time Cleanup
Re-installing your website from source, or worse… starting over, is not a fun process for most. An alternative option to cleaning up your website is to purchase a one-time cleanup that puts the cleanup of the website in the hands of professionals that know what they’re looking for.
Hostek is partnered with Sucuri, which allows us to offer their WAF/CDN product and their one-time cleanup service. Since we’re an official partner, we are able to offer this at a much more affordable cost.
On top of the website cleanup the Sucuri team will complete step #3 for you as well, which is the blacklist removal process. We highly recommend this option to ensure your website is clean.
Step 3: Delisting the Website From Blacklist
Once your website has been cleaned you will need to place an official re-scan of your website from Google. Most modern browsers rely on the Google website reputation feature in order to decide whether the website is safe from malware or not.
You definitely want to delist your website as quick as possible, since it has been reported that over 95% of website visitors leave the website when receiving the warning that the website contains malware. Additionally, search engines such as Google and Bing will flag your website as potential malware on Google search results and will also potentially drop your SEO rankings.
Once you have completed steps #1-2 in the sections above, then it’s time to request de-listing.
Google WebMaster Tools
- Open Google Webmaster Tools.
- Click Search Console and sign in with your Google account.
- Click Add a site.
- Type in your site’s URL and click Continue.
- Verify your site using the Recommended method or Alternate methods options.
- Click Verify.
- Check the Messages section to review any warnings.
If Google still believes your website is infected, then it will alert you to what it is seeing. If the new scan it performs comes back clean, then it will remove the blacklist for your domain and your visitors should no longer receive these warnings from Google (and some other browsers depending on Google).
Other Blacklist Recommend Checking
- McAfee SiteAdvisor
- Bing Blacklist
- Norton SafeWeb
- PhishTank
- Spamhaus
- BitDefender
- ESET
If a visitor to your website is using any AntiVirus program that has your website blacklisted, then their AV might block the request to your website. Several of the most popular AntiVirus programs are mentioned above.