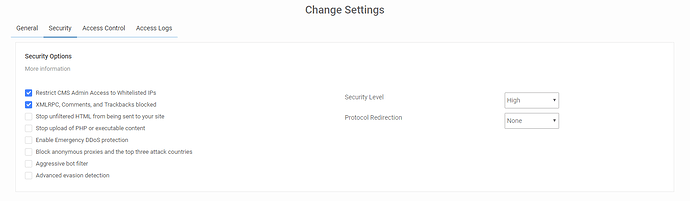
Security Settings
The ‘Security’ section will give you many options that can assist in further securing your site.
-
’Restrict CMS Admin Access to Whitelisted IPs’ - If this enabled the administrative backend will be inaccessible except for whitelisted IP’s. You can access the whitelisted IPs by navigating to the Access Control tab within your WAF dashboard.
Please Note: If your application is a membership site or allow anyone to create an account and log in there, do not enable this option -
’XMLRPC, Comments, and Trackbacks blocked’ - If your site does not allow for comments (trackbacks/pingbacks included), or if you use a 3rd party commenting system (Disqus, Facebook, etc…), you can block any comment attempt as it is likely spam.
-
’Stop unfiltered HTML from being sent to your site’ - This option will prevent users from sending or inserting unfiltered HTML content to your application. It will block elements like iframes and script calls from being used. Whitelisted IP addresses will not be affected by this setting.
Please Note: If your application has a forum or membership site that allows users to send messages and to post open content, do not enable this option. -
’Stop upload of PHP or executable content’ - This option will prevent PHP, Perl, or executable content from being uploaded. Whitelisted IPs will be unaffected by this option.
Please Note: We suggest enabling this option unless you allow users to upload files to your application. -
’Enable Emergency DDoS protection’ - The HTTP flood protection will prevent anyone from using a browser without JavaScript enabled from navigating to the site. This is very useful when the site is under DDoS. This option can be disabled when things normalize.
Please Note: This option may prevent legitimate users from accessing your site, and should only be enabled when your site is unavailable due to DDoS attacks. -
’Block anonymous proxies and the top three attack countries’ - This option, when enabled, will prevent traffic from China, Russia, or Turkey from interacting with your site. They will still be able to view content, but not register an account, submit comments, or attempt to log in. The same restriction applies to users using anonymous proxy services to hide their IP addresses.
-
’Aggressive bot filter’ - This setting will block user agents that do not match real browsers. This can include empty user agents, user agents that start with PHP/, and improper user agents from common browsers.
-
’Advanced evasion detection’ - This option will enable advanced evasion detection signatures. We recommend keeping this option enabled.
-
’Protocol Redirection’ - Allows you to specify if you would like all traffic redirected to https, HTTP, or to be determined by your application.
-
’Security Level’ - With this option you will have a choice between ‘High’ and ‘Paranoid’.
- ’High’ - This is the default security mode. This option enables all default security checks to prevent SQL injections, cross-site scripting, RFI, LFI, Security scanners and a number of attacks from ever touching your site. This also enables Virtual patching, so even if the application is outdated, it can’t be used to hack your site.
- ’Paranoid’ - This options includes all security options from the ‘High’ mode, but will also prevent POST requests. This means users will not be able to comment or send information to the site.